A manufacturing subcontractor in the defense industry has become the latest victim of hackers, Emsisoft, a cybersecurity and anti-malware company, told Fifth Domain.
Lockheed Martin, General Dynamics, Boeing and SpaceX are among dozens of companies named as victims of compromised data, accessed through the hacking of Visser Precision LLC, a Colorado-based aerospace, automotive and industrial parts manufacturer.
DoppelPaymer, a ransomware group, perpetrated the hack, according to Brett Callow, a threat analyst with Emsisoft.
[To see a photo (courtesy of Brett Callow/Emsisoft) posted to a hacker group website listing dozens of U.S. businesses whose data hackers claim to possess, click here.]
“Visser Precision, LLC was the recent target of a criminal cybersecurity incident, including access to or theft of data. The company continues its comprehensive investigation of the attack, and business is operating normally,” Visser Precision said in an emailed statement to Fifth Domain. “Visser Precision will continue full cooperation with its customer partner companies.”
The hacker group, which is a variant of actor BitPaymer, has been active for over a year but only recently began releasing compromised information, Callow said. The group’s website features an ominous message to “stay tuned” for a “LOT” more data to come “by parts.”
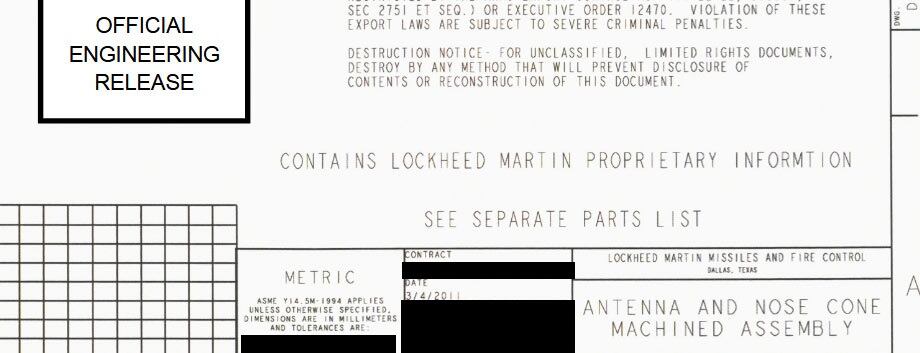
While threatening to release additional data, the group has already posted personnel information from industry corporations, government officials and subcontractors from 2016, as well as a partial document related to a missile antenna from Lockheed Martin from 2011.
“We are aware of the situation with Visser Precision and are following our standard response process for potential cyber incidents related to our supply chain,” a Lockheed Martin spokesperson told Fifth Domain. “Lockheed Martin has made and continues to make significant investments in cybersecurity, and uses industry-leading information security practices to protect sensitive information. This includes providing guidance to our suppliers, when appropriate, to assist them in enhancing their cybersecurity posture.”
Hacker groups — such as Maze, which previously released veterans’ sensitive information online — have targeted various government entities, law firms and businesses in the last year, as reported by Military Times, a sister publication of Fifth Domain.
Standard to other ransomware attacks, the hackers appear to have gained access to Visser Precision’s system, exfiltrating data before demanding payment to prevent a wider release.
“[The hackers] started by publishing older and less sensitive data,” Callow told Fifth Domain over email. “The more data they publish and the more sensitive that data is, the less incentive the company has to pay to prevent the remaining data being published.”
The Department of Defense recently announced an upcoming demonstration to test U.S. Air Force capabilities with SpaceX-developed Starlink technology. The released data, however, does not pertain to this platform.
SpaceX, General Dynamics and Boeing all did not immediately respond to requests for comments.
Callow, who monitors hackers’ activities, said DoppelPaymer has previously claimed in online posts to have stolen data in additional, unrelated incidents, and he believes more information will likely be released soon.
“This attack is particularly worrisome because of the nature of the information that may have fallen into the hands of cybercriminals,” Callow said. “Obviously, this [hack] could put the intellectual property of the companies’ concerned at risk and possibly even pose a risk to national security.”
The Federal Bureau of Investigation alerted businesses last October about “high-impact ransomware attacks” that specifically target government entities and corporations to encrypt data and unlock it for a fee, Fifth Domain previously reported.
In the last 48 hours, Maze separately published stolen information from a Canadian provincial government, state-owned Mexican petroleum company Pemex and a French telecommunications company, Callow added.
A 2019 Emsisoft report found that ransomware attacks targeted 113 state and municipal governments and agencies, 764 health care providers, and 89 universities, colleges and school districts nationwide.
Dylan Gresik is a reporting intern for Military Times through Northwestern University's Journalism Residency program.







